IP: 10.10.10.37
Enumeration
As we start off with a basic nmap scan: sudo nmap -sC -sV -O -p- -oA nmap/block 10.10.10.37, we get,
Ports open:
- 21/ftp
- 22/ssh
- 80/http
To access ftp, credentials were needed, so didn’t poke at that. Moved on to port 80 and the nmap scan showed that wordpress was running on it.
Default page when visiting the IP:
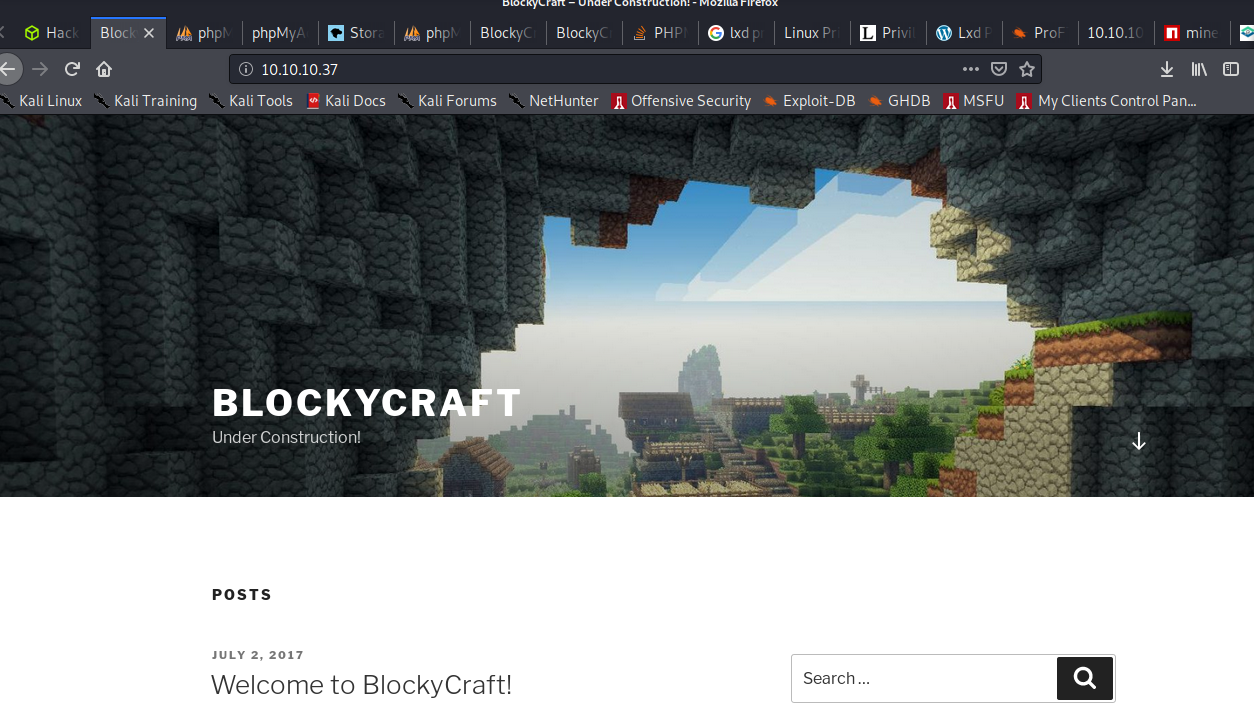
Running dirb I found out that phpmyadmin was also installed as well as wordpress. Then, wordpress need creds as well as phpmyadmin. So, the only way was to somehow find creds and login it to either of the 2 softwares.
So, used wpscan also (wpscan –url –enumerate vp,p,tt,t), but didn’t find anything interesting.
After googline, the ftp version had a rce, and after trying the exploit it wasn’t working. There was a 10.10.10.37/plugins directory which dirb had found.

It had 2 .jar files which are basically compiled java files. After downloading them, and unzipping them. .jar files are basically zip files. Then unzipping a .jar file and then using jad a java decompiler to decompile .class file which is basically compiled java file. Then, checking it out, it had creds!!!!!
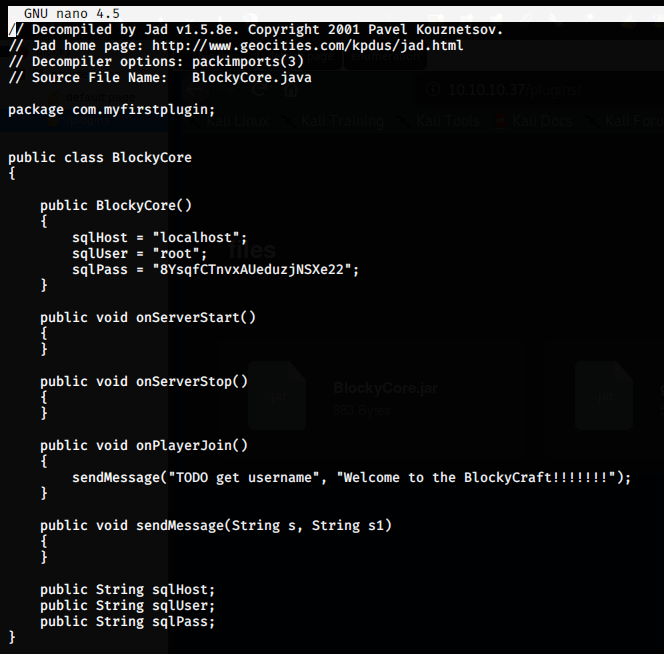
We tried these in phpmyadmin and go logged in!!!! After getting logged in we saw that there was a wordpress database which had wp_users table. Then, checking that out we found a hashed password and a username.
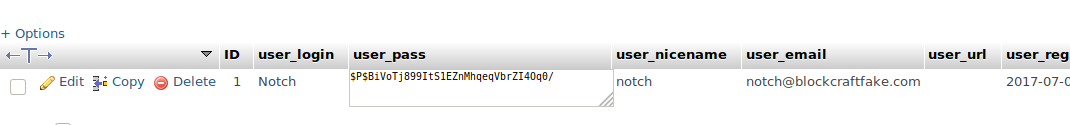
notch@blockcraftfake.com
We had got a username as: notch. And a hashed password: $P$BiVoTj899ItS1EZnMhqeqVbrZI4Oq0/
We just simply tried to ssh using this hash but we were unsuccessful. Then, we tried to use the previous creds from the .class file with the obtained username as: notch
AND BOOM!!!! We got a low privilege shell!!!!!
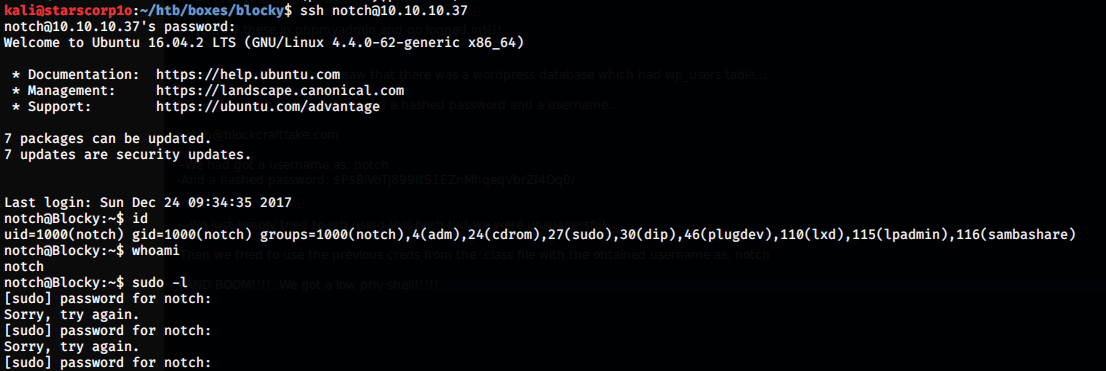
Privilege Escalation
Privilege escalation was a piece of cake!!!!
We used sudo -l to list the privileges and it asked us for the sudo password for the user notch. Then we entered the password obtained from the .class file and we got a list:
notch@Blocky:~$ sudo -l
[sudo] password for notch:
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALL
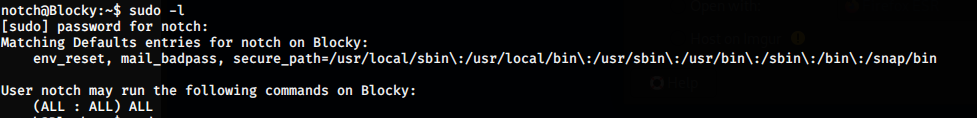
As we could see that we could run any commands as user notch. Hence, we just used sudo su to switch to the root user and BOOM!!!! We got a root shell!!!!!
notch@Blocky:~$ sudo su
root@Blocky:/home/notch# id
uid=0(root) gid=0(root) groups=0(root)
root@Blocky:/home/notch# ls
minecraft user.txt
root@Blocky:/home/notch# pwd
/home/notch
root@Blocky:/home/notch# cd /root
root@Blocky:~# ls
root.txt
root@Blocky:~# ls -la
total 28
drwx------ 3 root root 4096 Jul 14 2017 .
drwxr-xr-x 23 root root 4096 Jul 2 2017 ..
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwxr-xr-x 2 root root 4096 Jul 2 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 32 Jul 2 2017 root.txt
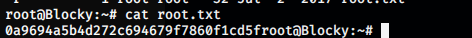
root@Blocky:~# cat root.txt
0a9694a5b4d272c694679f7860f1cd5froot@Blocky:~#
Now, we grabbed the root flag:
Important links or resources:
Check out Ippsec’s video on youtube about it -> https://www.youtube.com/watch?v=C2O-rilXA6I
Check out my previous post:
